Introduction
In this post I intend to give some definitions related with Injection Flaws, what are they? and how you can determine if your system might be vulnerable to this kind of attacks.
In a second part, I will show you some examples and some tips to help you detect and prevent this flaws.
What injection flaws are?
Injection is an entire class of attacks that rely on injecting data into a web application in order to facilitate the execution or interpretation of malicious data in an unexpected manner.
We can include Cross-Site Scripting (XSS), SQL Injection, Header Injection, Log Injection and Full Path Disclosure in this class, just to mention some examples.
The first two examples mentioned above, are the most usual used in this kind of attacks.
Usually, hackers just change the URL (in the location bar of browser for instance) adding an string that can be interpreted by system allowing to change the business logic of the system.
A classification of SQL injection attacking vector:
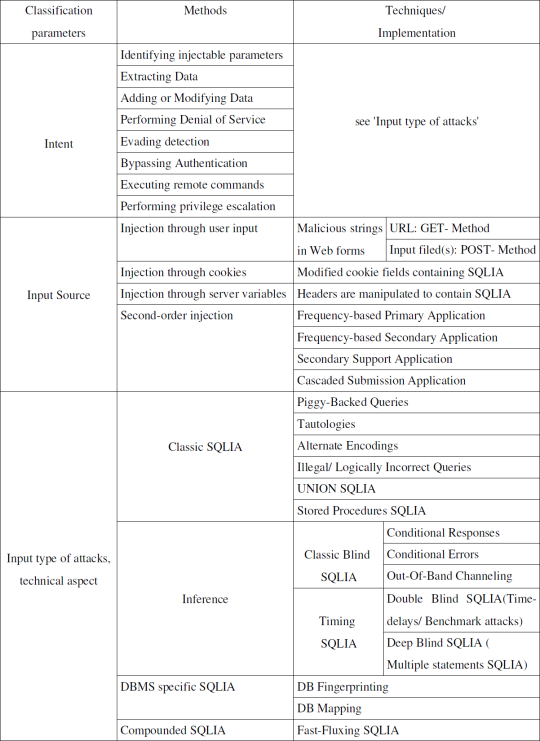
How to determine if you are vulnerable
The best way to determine if your applications are vulnerable to injection attacks is to search the source code for all calls to external resources (e.g., system, exec, fork, Runtime.exec, SQL queries, or whatever the syntax is for making requests to interpreters in your environment). Note that many languages have multiple ways to run external commands. Developers should review their code and search for all places where input from an HTTP request could possibly make its way into any of these calls. You should carefully examine each of these calls to be sure that the protection steps outlined below are followed.
